David S. Wall, Cybercrime Group, Centre for Criminal Justice Studies, University of Leeds, UK. <d.s.wall@leeds.ac.uk>
16 September 2020
During their attempts to recover from the Covid-19 lockdown recent attacks on both Newcastle Universities and others in the UK have highlighted how exposed the university sector is to cyberattacks. They are particularly vulnerable to Ransomware, which encrypts operating systems and steals data before extorting ransom payments to return the system to normal.
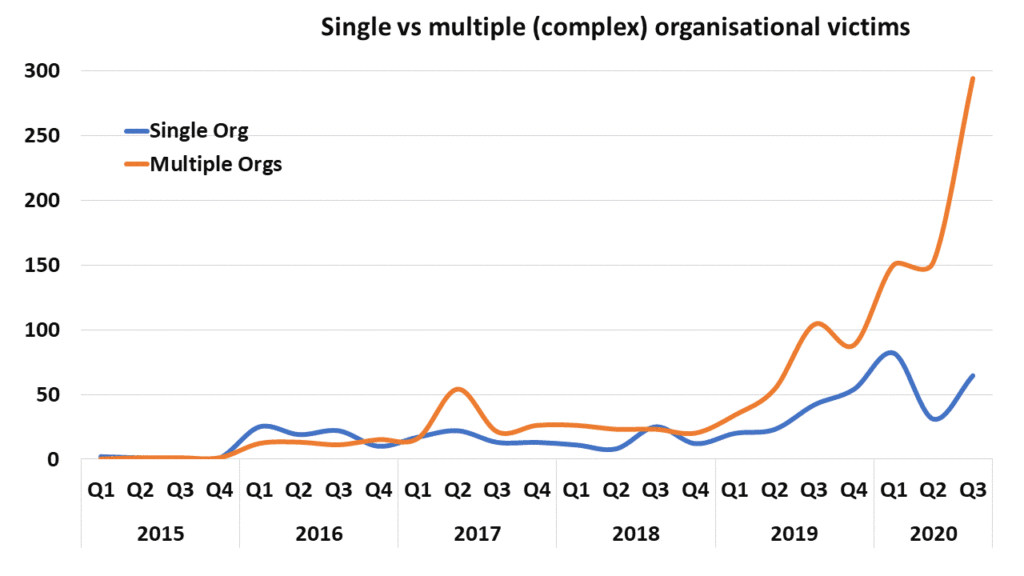
An analysis of a database of over 1650 attacks illustrates the modern cybercrime problem (EPSRC EP/M020576/1 / EP/P011772/1). It shows that there has been a suprising decline in attacks on the public sector this year during lockdown, especially healthcare. Yet, there has been a marked rise in attacks on the private sector. Interestingly, the analysis also indicates an increase in attacks upon large and complex businesses, which include Universities.
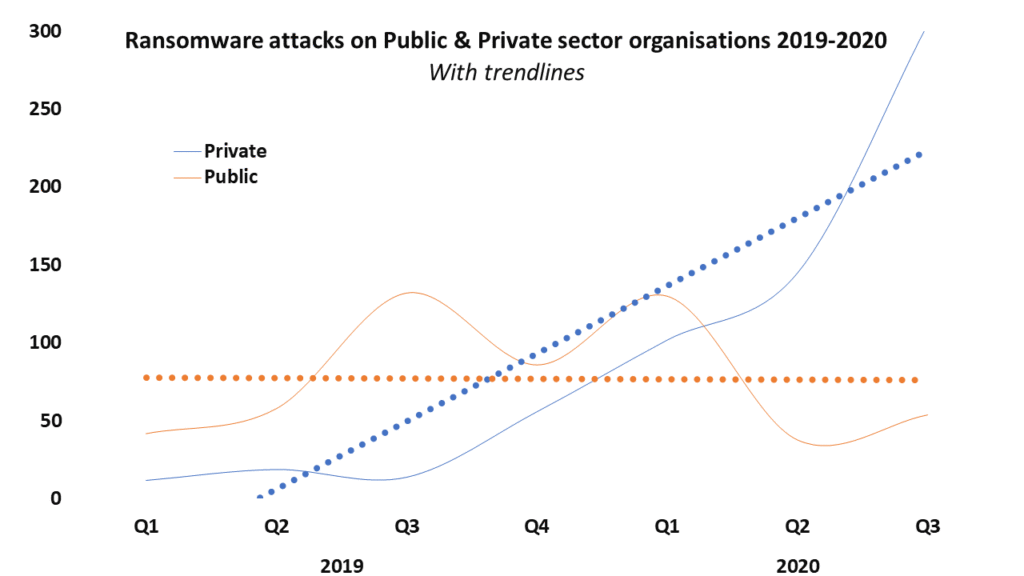
The graph below shows how attacks on larger organisations (multiples) have scaled their impact up and down the supply chain. They not only directly affect their clients, but also their client’s clients. We conservatively estimate that on average each attack impacts upon about 15 client organisations and in some cases many more.
Universities’ uniqueness exposes them to attack
Whilst Universities may operate on not-for-profit lines, they are still large complex business organisations, often with turnovers of £0.75 billion or more, so they are very attractive to economically motivated cybercriminals. University computer systems not only hold important trade secrets, which include research findings on Covid-19 vaccines amongst other large amounts of other research data, but they also hold important staff and student personal data, including exam results. So, they are attractive to both economic criminals and also spies. Furthermore, modern Universities are wholly dependent upon their IT systems to operate, so disruptions to the system can be economically damaging, which increases the leverage to pay the ransom when attacked. As mentioned earlier, their systems also have to be accessible quite deeply to staff and students, both locally and remotely.
Not only are Universities direct primary targets for attackers, but they also become secondary victims when their outsourced service suppliers are attacked. In May 2020 cloud computing provider Blackbaud was attacked by ransomware, and its many hundreds of clients (over 125 UK universities and NGOs and hundreds more worldwide) became secondary victims when their data, stored by Blackbaud, was potentially compromised.
A new generation of cybercrime
Ransomware attacks, such as this month’s Doppelpaymer attack on Newcastle, represent a new generation of cyberattacks. Since the second half of 2019, Ransomware groups (inc. Doppelpaymer which evolved from BitPaymer) have included the added fear tactic of ‘naming and shaming’ (or reverse double jeapoardy bis in idem). In contrast to the previous generation of ransomware, which relied on ‘spray and pray’ tactics, e.g. emailing millions of users with juicy subject lines in the expectation that a few would reply or open attachments, and in so doing, infect their computer, the new generation attacks are the result of careful research and planning by criminals and the targeting of senior managers to get their access. The new generation is strategically different from the old one.
Using stolen (or bought) login details, attackers enter the victim’s computing system and copy key organisational data before encrypting it. Reports suggest that attackers could have been in the system for a year to prepare the ground for the attack. In the past year they have also adopted a new tactic of publishing the victim’s name on a www site that they control along with some proof of attack. By publicly ‘naming and shaming’ victims, attackers can leverage the extortion of the ransom payment. Furthermore, attackers very often demand a ransom (sometimes in the £millions), which if not paid (in Bitcoin) within a set time period (such as 7 days) is doubled and more data is published. Some ransomware gangs ask for two ransoms, one for the encryption code to make the system work again and another to delete the sensitive data stolen. They also may even be prepared to negotiate down the final ransom amount to match the victim’s budget.
Protecting Universities
The question arises as to how Universities can protect themselves. Because of their known vulnerabilities Universities already undertake many additional measures to prevent attacks, for example, their attack prevention software repels millions of phishing attacks each month and stop malicious software entering their systems. Of course, being public and part of the UK they are also protected by the NCSC and the policing agencies.
The main problem lies in new and novel forms of attack, such as in Newcastle case, where the attackers enter the system and moved around it for some time preparing their eventual attack. Universities currently certainly manage their access account systems more effectively than before, but perhaps not enough. They also rigorously keep data backups. But backups do not necessarily get the operating system running again if it is damaged. The experience of many victims who have not paid the ransom is that they had to effectively pay for an entirely new IT system plus additional protection.
Should, then, victims ever pay ransom money to hackers?
Paying the ransom is not only frowned upon by policing agencies, but it is morally wrong and also feeds crime, thus encouraging criminals. Plus, there is not always the guarantee of a full return of data, despite assurances. But victims often face two dilemmas (in fact another double jeapoardy perhaps) the first is that paying the ransom can generally be much cheaper than not paying and having to reconstruct the entire system. The second dilemma is that the decision may be out of their hands as cyber-insurance companies often insist on paying and may even employ their own negotiators. With the knock-on effect that ransomware payments have risen.
The truth is that Universities, are not unique, like nearly all modern organisations which rely upon IT to operate, they regularly experience cyberattacks – to the point that university IT security staff are known to joke that DDoS attacks predictably increase during exam times. But the sobering fact of the modern age is that we are generally witnessing an increase in both the prevalence and also the enormity of cyberattacks via ransomware. In fact, any organisation that depends upon its IT systems to operate is vulnerable. In many ways the Newcastle Universities were simply unlucky in the lottery of cybervictimisation, however, they also have qualities, such as their openness, by nature of their constitution that leave them vulnerable.
The lesson from this and other recent ransomware attacks is to treat security like an arms race. Which means that security resources have to be applied, employing more staff who have uptodate skills in the field as the relevant IT skills sets change rapidly as the criminals become more skilled and practiced themselves. Any response has to be one step ahead of the continually shifting attack space, not alongside it.
The lesson from this and other recent ransomware attacks is to treat security like an arms race. Which means that security resources have to be applied, employing more staff who have uptodate skills in the field as the relevant IT skills sets change rapidly as the criminals become more skilled and practiced themselves. Any response has to be one step ahead of the continually shifting attack space, not alongside it.
Originally published as Wall, D.S. (2020) ‘Double Jeapoardy: Are Universities becoming the New Target for Cybercriminals and Spies?’, Computing, 11 Sept, https://www.computing.co.uk/opinion/4020075/double-jeopardy-universities-target-cybercriminals-spies (n.b. requires login) (this version contains additional information and links)
